GRACERMAUDITLOG SAP table for – Audit log Changes. Here we would like to draw your attention to GRACERMAUDITLOG table in SAP. As we know it is being mainly used with the SAP GRC-AC (Access Control in GRC) component which is coming under GRC module (Governance, Risk and Compliance). GRACERMAUDITLOG is a SAP standard transp table used for storing Audit log Changes related data in SAP. Could not execute 'EXPORT 'PUBLIC'.' AUDITLOG' INTO '/tmp/' SAP DBTech JDBC: 7: feature not supported: Exporting object PUBLIC objects owned by SYS user is not allowed.: line 1 c. SAP Knowledge Base Article - Preview. 2684434-How to export HANA audit log when audit trail target is internal database table. Cannot export audit log. Audit log report retrieves the data directly from SCU3 logs and helps to identify the changes done on GRC system. Customer wants to understand the tables that can be logged in order to retrieve the changes.
Syslog (default) − Logging system of Linux Operating System. Database Table − Internal database table, user who has Audit admin or Audit operator system privilege he can only run select operation on this table. CSV text − This type of audit trail is only used for test purpose in a non-production environment. SAP Security Audit Log (SAL) In the last article, we’ve discussed how to log/trace the critical table changes in a SAP system to meet one of the „business audit“ requirements. Let’s talk about one aspect of „security audit“ today. The weeknd beauty behind the madness download zip album.
Skip to end of metadataGo to start of metadataChange Documents:
1. Concept:
For changes to a commercial object to be able to be logged in a change document, the object must have been defined in the system as a change document object. A change document object definition contains the tables which represent a commercial object in the system. The definition can also specify whether the deletion of individual fields is to be documented. If a table contains fields whose values refer to units and currency fields, the associated table, containing the units and currencies, can also be specified.

It must be specified for each table, whether a commercial object contains only one (single case) or several (multiple case) records. For example, an order contains an order header and several order items. Normally one record for the order header and several records for the order items are passed to the change document creation when an order is changed.
Change document: A change document logs changes to a commercial object. The document is created independently of the actual database change. The change document structure is as follows:
- Change document header
The header data of the change to an object ID in a particular object class are stored in the change document header. The change document number is automatically issued.
- Change document item
The change document item contains the old and new values of a field for a particular change, and a change flag.
The change flag can take the following values:
- U(pdate)
Changed data. (Log entry for each changed field which was flagged in the Dictionary as 'change document-relevant')
- U(pdate)
- I(nsert)
Data inserted.
Changes: Log entry for the whole table record
Planned changes: Log entry for each table record field - D(elete)
Data were deleted (log entry for the whole table record) - I(ndividual field documentation)
Delete a table record with field documentation
1 log entry per field of the deleted table entry, the deleted text is saved
- I(nsert)
- Change document number
The change document number is issued when a change is logged, i.e. when the change document header is created by the change document creation function module (function group SCD0).
The change number is not the same as the change document number. The change document number is issued automatically by the function group SCD0 function modules when a change document is created for a change document object. The change number is issued by the user when changes are planned. The same change number can be used for various change document objects.
2. How to Create Change Documents Object:
a) Prerequisite: Transparent table for which Change Log has to be maintained.
Make sure that the field for which change log is to be maintained is checked as CHANGE DOCUMENT.
For this issue, double click the field and find the Table with New Content
NOTE: Check SY-SUBRC value before calling function-module 'YH1311_DETAILS_WRITE_DOCUMENT', since function-module will be called and inappropriate values get entered even if the insertion fails.
upd_icdtxt_yh1311_details = 'I', can be in I(nsert), U(pdate), D(elete) modes.
IF sy-subrc EQ 0.
CALL FUNCTION 'YH1311_DETAILS_WRITE_DOCUMENT'
EXPORTING
objectid = objectid
tcode = sy-tcode
utime = sy-uzeit
udate = sy-datum
username = sy-uname
* PLANNED_CHANGE_NUMBER = ' '
object_change_indicator = 'I'
* PLANNED_OR_REAL_CHANGES = ' '
* NO_CHANGE_POINTERS = ' '
upd_icdtxt_yh1311_details = 'I'
upd_zahack = 'I'
TABLES
icdtxt_yh1311_details = icdtxt_yh1311_details
xzahack = xzahack
yzahack = yzahack.
MESSAGE 'Log Created' TYPE 'S'.
ELSE.
MESSAGE 'Insert Error' TYPE 'S'.
ENDIF. ' IF SY-SUBRC EQ 0
STEP 4:
(MULTIPLE-CASE)
Create a field string for the database table 'zahack', including its all fields.DATA:
fs_emp TYPE zahack.
Create an Internal table for field string 'fs_emp'.DATA:
t_emp LIKE
STANDARD TABLE
OF fs_emp.
Create a field string and an internal table for 'Change Documents: Text Changes', to pass the changes made to the fields of 'zahack' table.
*---------------------------------------------------------------------*
* FIELD-STRING FOR CHANGE DOCUMENTS: TEXT CHANGES *
*---------------------------------------------------------------------*
DATA:
fs_cdtxt TYPE cdtxt.
*---------------------------------------------------------------------*
* TABLE FOR CHANGE DOCUMENTS: TEXT CHANGES *
*---------------------------------------------------------------------*
DATA:
t_cdtxt LIKE
STANDARD TABLE
OF fs_cdtxt.
Insert a record into 'zahack' table; simultaneously append data in 'ICDTXT_YH1311_DETAILS', 'XZAHACK' and 'YZAHACK'.
fs_emp-empid = 'YH1311'.
fs_emp-name = 'Tanveer'.
fs_emp-dept = 'ABAP'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
fs_emp-empid = 'YH1312'.
fs_emp-name = 'Sudha'.
fs_emp-dept = 'ABAP'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
fs_emp-empid = 'YH1313'.
fs_emp-name = 'Rama'.
fs_emp-dept = 'XI'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
fs_emp-empid = 'YH1314'.
fs_emp-name = 'Jyoti'.
fs_emp-dept = 'XI'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
fs_emp-empid = 'YH1315'.
fs_emp-name = 'Kiran Saka'.
fs_emp-dept = 'ABAP'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
fs_emp-empid = 'YH1316'.
fs_emp-name = 'Richa Tripathi'.
fs_emp-dept = 'ABAP'.
fs_emp-salary = '25000'.
APPEND fs_emp TO t_emp.
INSERT zahack FROM TABLE t_emp.
APPEND icdtxt_yh1311_details.
APPEND xzahack. ' Table with Old Content
APPEND yzahack. ' Table with New Content
upd_icdtxt_yh1311_details = 'I', can be in I(nsert), U(pdate), D(elete) modes.
IF sy-subrc EQ 0.
CALL FUNCTION 'YH1311_DETAILS_WRITE_DOCUMENT'
EXPORTING
objectid = objectid
tcode = sy-tcode
utime = sy-uzeit
udate = sy-datum
username = sy-uname
* PLANNED_CHANGE_NUMBER = ' '
object_change_indicator = 'I'
* PLANNED_OR_REAL_CHANGES = ' '
* NO_CHANGE_POINTERS = ' '
upd_icdtxt_yh1311_details = 'I'
upd_zahack = 'I'
TABLES
icdtxt_yh1311_details = icdtxt_yh1311_details
xzahack = xzahack
yzahack = yzahack.
MESSAGE 'Log Created' TYPE 'S'.
ELSE.
MESSAGE 'Insert Error' TYPE 'S'.
ENDIF. ' IF SY-SUBRC EQ 0
STEP 5: Open 'CDHDR' - 'Change Document Header'.
Utilities->Table Contents-> Display.

Enter change document object name and execute (F8).
Similarly, open 'CDPOS' - 'Change Document Item', to draw items information.
NOTE: In the above example, we tried with only I(nsert), in the same fashion U(pdate), D(elete) can also be tried.
This post introduces SAP® Security Audit Log.
Overview
According toSAP:The Security Audit Log records “security-related system information such as changes touser master records or unsuccessful login attempts. This log is a tool designed forauditors who need to take a detailed look at what occurs in the AS ABAP system. Byactivating the audit log, [the SAP system keeps a record] of those activities that youspecify for your audit. [Customers] can then access this information for evaluation in theform of an audit analysis report.
“The Security Audit Log provides for a long-term data access. The audit files are retaineduntil you explicitly delete them. Currently, the Security Audit Log does not support theautomatic archiving of the log files; however, you can manually archive them at any time.
“You can record the following information in the Security Audit Log:
- Successful and unsuccessful dialog login attempts
- Successful and unsuccessful RFC login attempts
- RFC calls to function modules
- Changes to user master records
- Successful and unsuccessful transaction starts
- Changes to the audit configuration”
According to Enterprise Threat Monitor:“SAP security audit log is the main location for the traces of events triggered by thesystem or by applications, which are related to security. [It is in the form of a table.]Based on the configuration which event types must be recorded, it saves the data to thedisk on the SAP application server instance.” Specify the audit files location by settingthe profile parameter, rsau/local/file, in the SAP system.
A SAP blogadds: “Since security audit logs are stored on the file system and not the database, they[do not impact performance]. The main consideration of the operations teams is the storagerequirements. Based on the activated event types (audit classes), the data volume [can vary].”
Configuration of Security Audit log
There are two configuration options in the security audit log:
- Set Profile parameters
- Use appropriate filter configuration using SM19 or RSAU_CONFIG
1. Profile parameters
Set profile parameters based on your release.
A) For releases earlier than 740: In the default profile, default.pfl, of the system,set the following profile parameters:
- rsau/enable=1
- rsau/user_selection=1
- rsau/selection_slots=10 (or higher)
- rsau/integrity=1 (if available - see SAP Notes 2033317 and 1810913)
Sap Audit Log Table Lamp
B) For releases 740 to 751: Call transaction SM19. Activate the SecurityAudit Log by performing the following steps:
- Select the Security Audit active checkbox on the Kernel Parameters tab.
- Activate both Generic User Selection and Integrity Protection Format.
- Set the number of selection filters to at least 10.
C) For releases 752 and later: Call transaction RSAU_CONFIG. Activate the Security AuditLog by performing the following steps:
- Select the Static security audit active checkbox underSecurity Audit Log Configuration -> Parameters in the tree.
- Activate both Generic User Selection and Integrity protection format active.
- Set the Number of Filters per Profile to 10, which is the minimum requirement.
Note: When you use the Kernel parameters in the Security Audit Log configuration (step1B or 1C), existing settings with the same name in the system’s profile are ignored. Formore information, seeSAP Note 539404,answer 1a.
2. Setting up appropriate filter configurations
To set up filters, perform the following steps:
Call transaction SM19 or RSAU_CONFIG. Create a new profile.
Create the following filters:
- All clients (
*), userSAP#*: Record all events. The character#serves to mask*as non-wildcard. - All clients (
*), user<your emergency user IDs>*: Record all events. - Client 066, all users (
*): Record all events. - All clients (
*), all users (*): Record all events except AUW, AU5, AUK, CUV, DUR,and EUE (deactivate via Detailed Display).
- All clients (
Save and activate the profile.
Finally, check the configuration. If you have made changes to the profile parameters orthe static profile, restart the system to make them effective. Until you can restart thesystem: Convert the static profile to a dynamic profile and activate it.
Analysis of Security Audit log
Call transaction SM20/SM20N, or its equivalent transaction depending on your SAPNetweaver version (see the following table), and give the required selection criteria asinput. Click Reread Audit log to get the configured audit log for your system.
Table: Old and New functions of Transactions and reports related to the Security Audit Log
Table Source: https://blogs.sap.com/2014/12/11/analysis-and-recommended-settings-of-the-security-audit-log-sm19-sm20/#jive_content_id_Recommended_Settings_for_the_Security_Audit_Log_SM19__SM20
According to aSAP blog post:“You can view the long text of the Security Audit Log event messages using transactionSE92 (or in transaction SE61 if you choose the document class SL (Syslog). Usingnote 1970644, you can get reportRSAU_INFO_SYAG which shows all the events of the Security Audit Log including thecurrent status of activation. The detail view allows you to create a HTML-based eventdefinition print list including the full documentation.”
It primarily depends on customer requirements to enable all successful and non-successfulevents for all clients and users. TheSAP postcontinues: “There is no performance impact, not in time nor in space, if you logunsuccessful (=critical) events as these events happens rarely. As soon as you start loggingsuccessful events you might look to space—the growing size of the auditfiles—but still not to time, as the Security Audit Log is optimized for speed.”
Sap Audit Log Table 2019
SAP offers functionality to email Security Audit Logs with the help of reportsRSAU_SELECT_EVENTS or RSAU_READ_LOG. Schedule any of these reports as a backgroundjob to receive the audit log from the SAP system.
Sap Audit Tools
The following table gives an overview of the critical events messages store in the auditlog for different audit classes.
Table: Critical events of Dialog, Transaction, RFC, and User audit classes
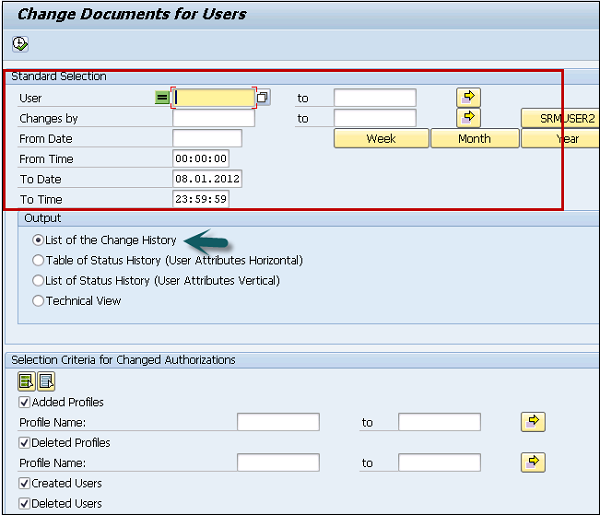
Table source: (https://blogs.sap.com/2014/12/11/analysis-and-recommended-settings-of-the-security-audit-log-sm19-sm20/#jive_content_id_Recommended_Settings_for_the_Security_Audit_Log_SM19__SM20)[https://blogs.sap.com/2014/12/11/analysis-and-recommended-settings-of-the-security-audit-log-sm19-sm20/#jive_content_id_Recommended_Settings_for_the_Security_Audit_Log_SM19__SM20]
Conclusion
Switching on Security Audit log for all the clients and users is a crucial step in securityas it provides detailed information on the audit reports. Its benefits far outweigh itscosts and provide long term data access. I strongly recommended that you enable SecurityAudit log, especially in production environments.
Use the Feedback tab to make any comments or ask questions. You can also clickSales Chat to chat now and start the conversation.
